How to protect your business against zero-day attacks
Did you know that worldwide 92 malware attacks happen every minute and out of these, 69% of them are zero-day? Worryingly, this is significantly higher in the UK where a huge 96% of malware attacks are zero-day. Let’s take a deeper look into zero day threats and attacks and the steps you can take to help protect your business.
What is a zero-day threat?
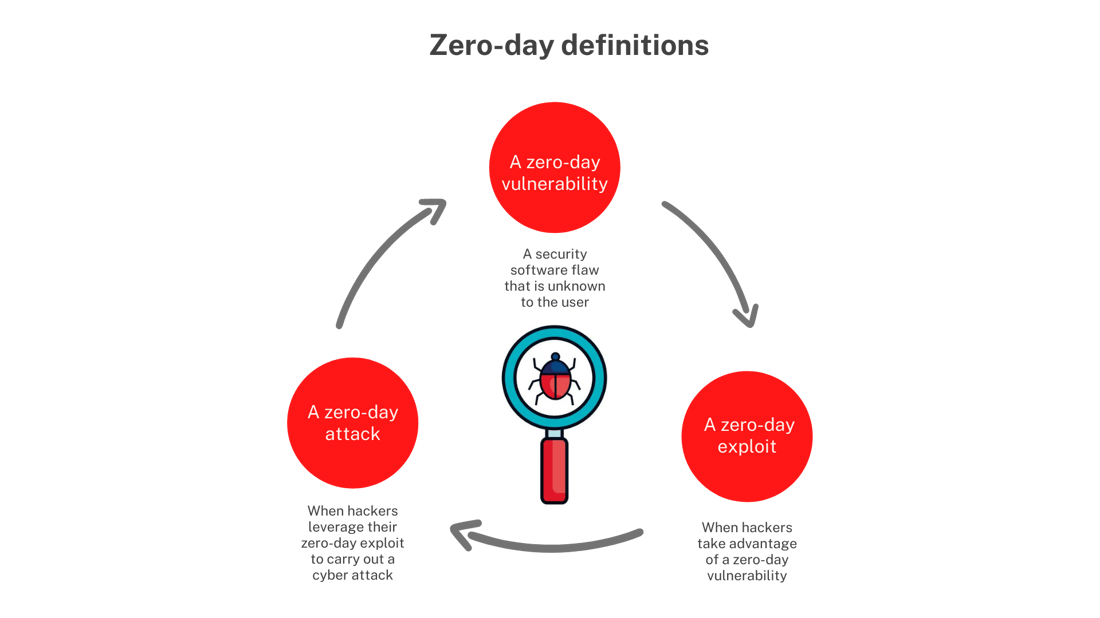
A zero-day threat is a malware threat that hasn’t been seen before and doesn’t match any known malware signatures which means that it can’t be detected by signature-matching software.
This threat might exploit an unknown software vulnerability, referred to as a zero-day vulnerability, or it might be a new type of malware delivered by traditional means.
A zero-day exploit is when hackers take advantage of a zero-day vulnerability to carry out a cyber attack. When a zero-day attack is detected, it must be mitigated as quickly as possible as software developers have no patch to fix it.
Why should you be concerned about zero-day threats?
Cyber attacks are becoming more and more prevalent and new zero-day threats are originating at an alarming rate. In order to protect your network, applications and data, it is vital to implement cyber security best practices in your business and have an advanced threat prevention system in place which will verify untrusted files, emails and links before they enter your network.
How can you protect your business against zero-day attacks?
Although the nature of zero-day malware threats mean that we cannot see them coming, there are still various ways you can help to protect your business against zero-day attacks.
- Keep your software up to date to ensure that security patches are in place and reduce the risk of malware infection
- Use a firewall to monitor and block suspicious activity
- Use an antivirus software to protect you against known and unknown threats
- Ensure your team is educated on zero-day threats and seek out solutions when zero-day vulnerabilities are discovered
- Limit the amount of applications you use, as the less you download, the less data you are putting at risk
Advanced Security Protection
In today’s climate, a basic firewall is no longer enough to protect your business against cyber security threats. In order to fully protect your business, you need a full set of scanning engines to safeguard your network against viruses, spyware, malicious apps and data leaks, from ransomware to botnets to zero day malware. An advanced network security solution will address all aspects of threat prevention, detection, correlation and response, including both current and evolving threats.
What should your security protection include?
Cloud Sandboxing
Organisations of all sizes are falling victim to sophisticated cyber attacks that get past traditional signature-based defences, causing loss of personal information, millions of pounds and permanent reputation damage. Cloud sandboxes simulate physical hardware, including CPU and memory, exposing malware which is designed to recognise and evade traditional network security defences. This full system emulation provides the most comprehensive level of protection against advanced malware. It uses behavioural analysis to establish if a file is malicious and identifies and submits any suspicious files to a cloud-based sandbox. Here, the code is emulated, executed, and analysed to determine its threat potential. If the file is found to be malicious, action is quickly taken to ensure your network and digital assets remain secure.
AI-Powered Anti-Malware
Signature-based anti-virus solutions are only able to detect known threats, whereas AI-powered anti-malware uses a machine-learning engine which can predict threats months before they are released, providing powerful protection for your small or medium-sized business. AI-powered anti-malware works by breaking millions of files down into their fundamental building blocks and then examining the characteristics of every file for signs of malicious intent. This produces a series of statistical algorithms that can classify files against the fingerprint of malicious and non-malicious files to determine whether a file is safe to run before it is executed. The process is automated and delivers results within fractions of seconds and in real time. As modern malware mutates at an incredible rate and can change hour by hour, human-produced signature-based virus detection is rapidly becoming obsolete.
DNS Filtering
Hackers rely on DNS to carry out cyber attacks, so careful inspection of DNS requests is a key way to identify and intercept attacks. DNS filtering detects and blocks potentially dangerous sites, protecting your network and team from damaging malware infections. When a user tries to connect to a known malicious DNS address, they are automatically blocked and seamlessly redirected to a safe landing page. Cloud-based DNS filtering services are efficient and save your business time and money as there is no software or additional hardware to maintain.
Network and Endpoint Threat Correlation
Whether you have offices across multiple sites or employees working from different locations outside of your network, it can be challenging to manage security consistently and cohesively across your organisation. It is extremely important for businesses to have visibility into their network and endpoint event data and be able to quickly and efficiently leverage actionable insight to remove threats. A key component of TDR is the collection and analysis of event data. Event data is analysed against enterprise-grade threat intelligence feeds using a proprietary algorithm and assigned a comprehensive score and rank based on threat severity. This allows your IT team to respond to threats quickly and confidently, ensuring that you stop malware attacks before they have time to infect your entire organisation.
Cyber Security
Our cyber security solutions provide the latest in security protection technology to help your business counteract cyber security threats.
EBC Group offer the most advanced cyber security solutions to provide your business with the maximum possible protection against cyber attacks. We offer two security protection packages to suit your business needs. Our basic security protection package comprises multi-layered protection, including IPS, antivirus, URL filtering, application control, spam blocking and reputation lookup. Our advanced package includes all of the features of our basic package plus AI-powered malware protection, enhanced network visibility, endpoint protection, cloud sandboxing and DNS filtering for a fully-encompassing security solution.
We provide our comprehensive cyber security solutions, comprising cyber security protection, testing and training, alongside our range of fully managed IT services. Speak to us today about how we can help you secure your business. Contact us online, call us on 0121 3680119 or email us at hello@ebcgroup.co.uk.


