EBC Group's Cyber Security Event - 26/03/24
EBC Group’s Cyber Security Event explores navigating the complexities of modern digital threats to fortifying your businesses defences against emerging cyber risks, we're here to empower you with the knowledge, tools, and strategies needed to stay ahead in the fight against cybercrime.

EBC Group
Cyber Security Event
Tuesday 26th March 2024
On Tuesday 26th March, EBC Group hosted a cyber event in the EBC suite at the Worcestershire County Cricket Club.
This was our forthcoming cyber event, in which we focused on the crucial significance of robust digital defences for safeguarding businesses.
We had a lineup of esteemed guest speakers, whom of which are all prominent figures in the cybersecurity realm, with the likes of Andre Lynch from Connectwise, Duncan Sutcliffe from Sutcliffe & Co Insurance Brokers and our very own Mike Cook & John MacDonald from EBC Group.
To conclude this event, we offered a FREE dark web scan for all the businesses present in the audience, in which they would scan a QR code on the screen and we would sit down with them and show them just how much of their businesses sensitive data has been leaked on the dark web in order to reflect the presentations presented and support the point that not having a robust cyber security plan in place is just not an option in 2024.
Mike Cook - EBC Group
Mike Cook began by welcoming all and going on to share some eye-opening cyber crime statistics, of which were:
Cyber Security was identified as a Tier 1 threat in the 2010 National Security Strategy, alongside Terrorism, War and Natural Disasters.
Cyber Security is the most common crime type experienced in the UK yet there are less than 2% of Police resources aligned to investigations.
Mike then highlighted the fact that cyber crime is now a recognised industry, with tools to carry out cyber crime available all over the internet, and even Amazon having a Top 10 list of tools that are being sold on their platform. Cybercrime in itself is now a multibillion pound industry worldwide Sophistication and volume of attacks now off the scale. Doing nothing to protect your business is simply not an option.
Andre Lynch - ConnectWise
Andre Lynch was then welcomed to the floor with his presentation on 'How Cyber Security Keeps Your Business Safe'. Andres presentation highlighted Todays Landscape, The Risks Businesses Face in 2024, What Is "Good" Cyber Security and How to Build Cyber Resilience.
Andre showed us an array of recent media that documented cyber attacks, ransomware demands, data breaches, demonstrating the diversity of attacks present in todays world. Andre asked how many in the audience have heard about all 10 cyber attacks and who could name them, these being:
1. Phishing
2. MITM
3. BYOVD
4. Ransomware as a Service
5. Dark Web
6. Fileless Malware
7. Zero Day Attack
8. APT
9. Mimikatz
10. Triple Extortion Ransomware
What is the impact of an attack on your business? Andre shared the following statistics on the matter:
Average ransomware dwell time - 21 days
Ransoms Demand Charges - 10% of annual revenue
Average costs of recovery following a cyber attack - £ 1.4 million
Average downtime that follows a cyber attack - 21 days
Legislation - fines/legal action
Insurance
IBM recently published the Phenomenon Study which showed that the customers who had Advanced cyber services in place still had cyber crime, but the cost was lowered by some 80% primarily because the downtime and impact was reduced by picking up the issue earlier.
The topic of AI was also covered in which Andre asked everyone to think about how new AI still is to us, but what amazing things it is already capable of. He asked us to think just how much has changed since the first iPhone initially released back in 2007 for example, what capabilities it had back then in comparison to everything it is capable of doing now. These are things like Front Facing Cameras, Wireless Charging, Credit/Debit Card Payments, Face ID/Touch ID, Health Monitoring, GPS Navigation, the list goes on. If we apply this iPhone evolution to the idea of AI, what will AI hold for us in 17 years time? Whilst there are benefits, we must also consider the dangers that could follow.
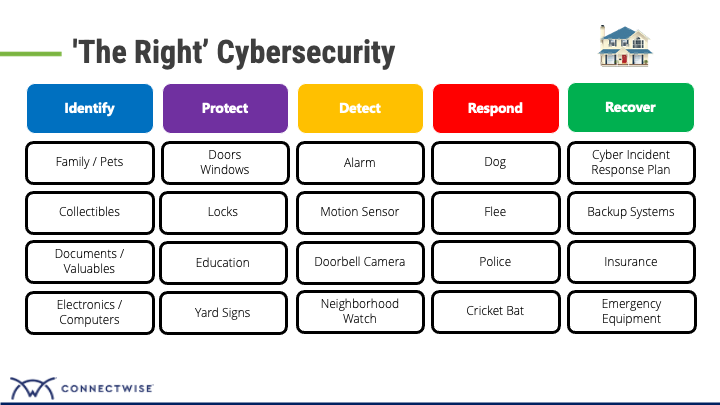
What is in your home?, Your belongings – what is important to you?, How do you keep people out?, How would you detect if an uninvited guest showed up?, How do you respond?
In Security, we call these:
Identify – asset inventory
Protect – Firewall, EDR
Detect – EDR, MDR (EDR+SOC) & SIEM
Respond – Isolation and containment, Triage , call your TSP, Cyber Ins, call FBI or authority’s ,
Recover – Follow your IR plan, Cyber Ins, restore backups
How do you get a comprehensive cyber security solution?, It’s all about having those different layers of security to address the unique risks and threat to your business.
Duncan Sutcliffe - Sutcliffe & Co Insurance Brokers
Duncan Spoke to us about the Importance of Effective Insurance
Businesses have procedures, polices, certifications & training to protect equipment, property, staff & customers. But despite all the protective and preventative measures, it's vital to also protect yourself by having insurance in place.
Natural disasters are something we don't always account for because we never think they will happen to us, but the reality is, whilst not often, do happen. If they do occur, the damage can be financially catastrophic.
Duncan then presented us with some statistics surrounding online fraud:
"Since 2018 there has been more cyber enabled crime
than all other crimes combined"
"SMEs are 40% more likely to be a victim of
cyber crime than burglary"
"67% of cyber incidents were caused directly by employee error, negligence or social engineering."
Your business, suppliers, customers & family are all reliant on data and electronic communication, so how would you cope if you lost access to that data or means to communicate? and what would happen if that data was to be stolen or corrupted?
Data that we rely upon are things like: Databases, Email, Websites, GPS, Telematics, CAD, Barcodes, EPOS, RFID, Just-In-Time, BIM, Stock Control, CRM, Big Data, Smart, Social Media, BYOD, VOIP, EDI, Contactless, Cloud, Bluetooth, Wi-Fi, IOT... the list goes on. Similar to Andre's point about what iPhones are now capable of doing, can we really risk not safeguarding this data?
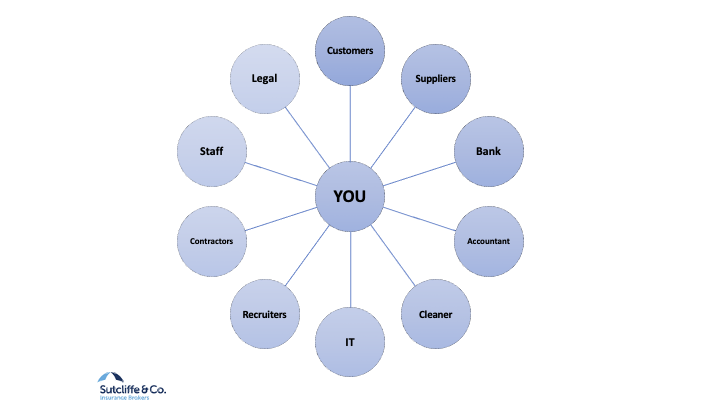
Your business has a vast web of connections, coming in and going out, and each of these connection also have a vast web of connections going in and out. You want to be able to control what comes in and out, and who has access to this information.
Duncan touched upon the importance of educating staff in the world of cyber security, and how 67% of cyber incidents were caused directly by employee error, negligence or social engineering. It's incredibly important that staff are able to spot fake emails. Clicking upon spoof emails, links embedded within, and filling out details that are not from a trusted source can create a realm of issues. If the financial department wasn't entirely clued up on their cyber training and were sent an invoice posing to be from one of their clients, then there is a risk that they could fill this out via the fake email and hand over all sorts of financial data to a scammer. This only has to happen once before your business is under financial threat.
Another example of this is a story that Duncan shared. A company he knew that found a USB stick in their car park. The employee picked this up and plugged it into their laptop to try to see if they could find out who this belonged to, however what they were unaware of is that this USB stick was strategically planted there from an external source in hope someone would pick it up and plug it into their machine. Unfortunately, this USB contained a virus which infiltrated the business and provided the hacker with all sorts of sensitive information. This was something that the staff member never even considered nor knew was a possibility. It's these types of attacks that staff members are often unaware of.
John MacDonald - EBC Group
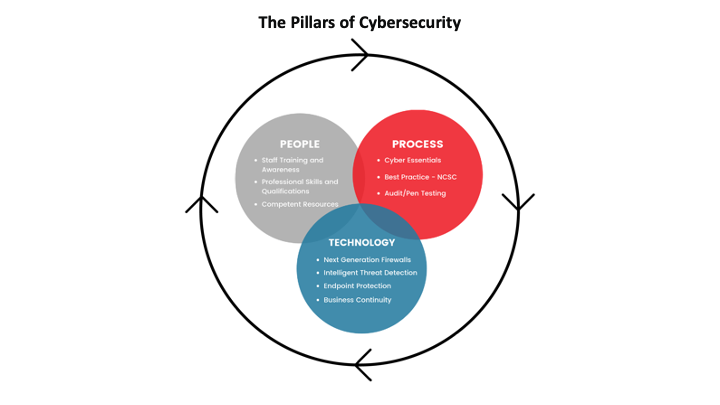
The last speaker of the day was our one and only, John MacDonald. John led with "Cyber Security is not just about technology"
People: The human element is often considered the weakest link in cyber security, but it's also one of the most important. This pillar encompasses everything from security training and awareness to the behaviours and attitudes of employees.
Process: This pillar is about having the right policies, procedures, and governance structures in place. It's crucial to establish standardised methods for how things are done to minimise risk and ensure consistency.
Technology: While people can create vulnerabilities, technology can help prevent, detect, and respond to cyber threats. This pillar involves the use of hardware and software tools to protect systems and data. Firewalls, antivirus software, encryption tools, intrusion detection systems, and other cyber security technologies are critical components. However, technology alone is not sufficient to protect against cyber threats. It must be combined with educated people and effective processes to be truly effective.
John then went into the topic of 'Why is cyber security is important for businesses?'. In today's digitally interconnected world, the threat of a cyber attack looms large over businesses of all sizes and sectors. The consequences of a cyber attacks extend far beyond mere financial losses. John then went on to explore some of the critical implications that businesses face in the event of a cyber breach:
Financial Losses: A single cyber attack can cause irreparable damage to a business’s finances, reputation, and legal standing.
Damage to Reputation: A cyber attack can impact a business’s reputation. Customers expect companies to safeguard their personal information, and a data breach can quickly erode Trust and credibility.
Legal Liabilities: Legal liabilities are also a significant concern for enterprises that experience a cyber attack. If a company fails to protect its customers’ data and a breach occurs, it may be held legally responsible for any damages.
Prevention of Intellectual Property Theft: Cyber security’s critical role in ensuring business survival is preventing intellectual property theft. Intellectual property includes a company’s trade secrets, patents, trademarks, and copyrights.
Compliance related to cyber security. Failure to comply with regulatory requirements: In many industries, companies must comply with various regulatory requirements with these regulations can result in significant fines and legal penalties.
“We’re a small company. The biggest issue is trying to survive on a week-by-week basis. We can’t afford to allocate sums to cyber security. I’ll spend it as and when I have it, or when I need to.”
– Managing director, small business
“We’re not on the radar of international actors. We’re flying under the radar.”
– Finance Manager, medium business
“The biggest issue is people. People get things wrong, and it’s really difficult to plan how they’ll get it wrong.”
– Systems and Infrastructure Manager, large business
John then explored the different reasons that businesses are being hit with cyber issues. As businesses navigate the ever-expanding digital landscape, several challenges emerge in the realm of cyber security. From under-investing in IT infrastructure to complacency or denial regarding potential threats, organisations face a myriad of obstacles in safeguarding their data and systems.
Additionally, a lack of awareness regarding the extent of cyber risks further compounds these challenges. The complexity of the cyber security field, characterised by rapid evolution and intricate technologies, presents a daunting task for businesses seeking to fortify their defences.
Under-investing: in IT in general, especially in Cyber securityComplacency or Denial: The "it won't happen to me" mindset
Lack of Awareness: Not all businesses understand the full extent of cyber risks
Complexity: The field of cyber security is complex and rapidly evolving
John touched on the idea that some businesses are under the impression that having a firewall in place is the be all and and all of cybersecurity. But this isn't the case, and why do you need more than just a firewall?
While firewalls are an essential component of a solid Cyber Security strategy, they represent just one layer of protection. Firewalls primarily protect against unwanted intrusion attempts from the outside, based on predefined rules and policies. However, what happens when you work from home?
Cyber Security today requires a layered, comprehensive approach. Firewalls, while important, only provide one level of defence. Adding MDR / SOC and SIEM elements can provide more robust protection against a wider range of threats.
John then moved onto anti-virus, EDR and SIEM. Having an anti-virus will not keep a hacker out of your business, as it can only detect previously known threats, it cannot detect unknown threats and is based on file signatures that can easily be tricked.
EDR can detect previously known and unknown threats due to behavioural based monitoring, complex and detailed endpoint data collection and has added features and benefits including application monitoring, threat hunting capabilities, and advanced reporting.
But why is EDR not good enough? EDR is just the start, EDR (Endpoint Detection and Response) + SOC (Security Operations Centre) = MDR (Managed, Detection & Response)
And this then brings us to SIEM (Security Information and Event Management). A SIEM works by collecting log and event data generated by devices, and applications. It then brings them into a central platform for analysis and reporting. When the SIEM identifies a threat through a set of predetermined rules, an alert is generated for human review. Why is this needed? For auditing and compliance requirements, full visibility of everything happening within the network, a SIEM dramatically decreases the time it takes to identify threats and also provides detailed forensic analysis in the event of major security breaches.
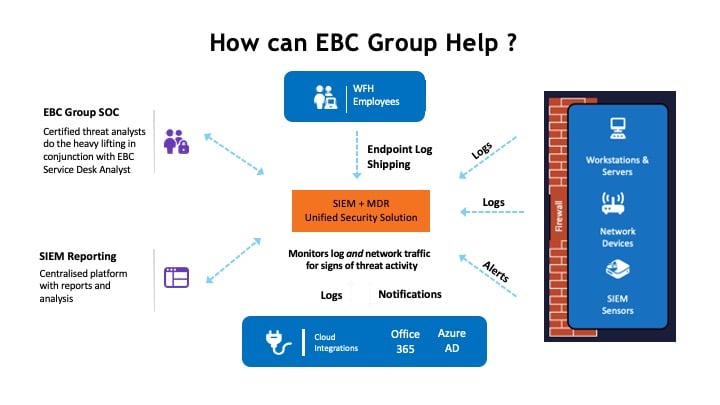
How can EBC Group help?
EDR: We provide the EDR platform, which uses advanced detection techniques to carry out threat hunting against known and unknown attack patterns while using AI to detect suspicious behaviours and signatures.
MDR (24/7 SOC): We also provide MDR which takes our Endpoint Detection and Response to the next level, by overlaying a fully managed 24/7 human-led SOC team to monitor, investigate and remediate any security incidents.
For more information about the event or to enquire about future events and opportunities, please contact EBC Group at hello@ebcgroup.co.uk or 0121 368 0154.
About EBC Group
EBC Group are an award-winning managed IT service provider of IT & Telephony Solutions, Cloud hosting, Cyber Security, Print & Data Solutions.
As an integrated managed IT service provider, EBC Group plan, implement and support their client’s IT and technology, enabling them to run their business smoothly and securely. EBC Group have been providing technology solutions for 35 years to ensure their clients businesses are running efficiently at all levels of their operations.
Address: 221 Hagley Road, Hayley Green, Halesowen, West Midlands, B63 1ED
Website: www.ebcgroup.co.uk
Social Media
LinkedIn: ebc-group
Twitter: ebc_group
Instagram: @ebc_group_


